Home / Blog / Securing Hybrid Workloads with Service Perimeters
Hybrid workloads can be described as a configuration in which workloads are deployed across multiple computing environments, one based in the public cloud and at least one being private.
There are several ways to connect on-premises workloads with Google Cloud APIs and Services. For example, you could consume them directly via their internet-facing endpoints, through a Cloud VPN, or work with a dedicated partner to enable Cloud Interconnect.
This blog post will look at how Service Perimeters and Private Google Access can help secure hybrid workloads.
What’s a Service Perimeter?
A service perimeter is a security boundary that you can configure to control communications between your compute resources and Google Cloud APIs and Services. It allows free communication inside the perimeter but blocks all communication crossing the perimeter.
Service Perimeters are defined as VPC Service Controls at the Organization level in Google Cloud. VPC Service Perimeters function like a firewall for GCP APIs.

Using VPC Service controls, you can restrict access to selected APIs to only authorized projects or service accounts. These service controls provide an extra layer of security that is independent of Identity and Access Management.
What’s Private Google Access?
Private Google Access is a way for on-premises hosts to connect to Google APIs and services by routing traffic through a Cloud VPN Tunnel or a Cloud Interconnect instead of across the internet. Private Google Access allows hosts and workloads in a VPC or on-premise network configured with private (RFC1918) IP addresses to securely connect to the APIs and services.
Google publishes DNS records for two Virtual IPs (VIPs) to enable private access: private.googleapis.com and restricted.googleapis.com. All requests for APIs and services that use either of these two VIPs are routed through Google’s network.
- private.googleapis.com enables access to most Google APIs and services, whether VPC service controls support them or not. This includes the APIs for Maps, Google Ads, and Google Cloud.
- restricted.googleapis.com VIP restricts API access to only the APIs and Services supported by VPC Service controls. Access to APIs and services that aren’t supported is blocked.
Bringing it all together
Let’s look at an example use case to illustrate how to use these features together to secure a hybrid workload.
Acme Co., a data processing company, is migrating an in-house application to Anthos GKE on VMware. The application processes documents containing hand-written notes and transcribes the handwritten information with the Cloud Vision API. They also consume other Google services, such as Cloud CDN, for their website and other services needed to support their business.
Acme Co. can leverage Private Google Access, Cloud Interconnect, and service perimeters to restrict access to the APIs and services needed by the application.
To securely route requests from their Anthos GKE environment without interrupting access to the other services needed by the business, they configure access to private.googleapis.com by creating the appropriate DNS entries in their on-premises DNS provider. This allows the on-premise environment to interact with the Google Cloud APIs needed through the Cloud Interconnect without impacting access to other Google APIs.
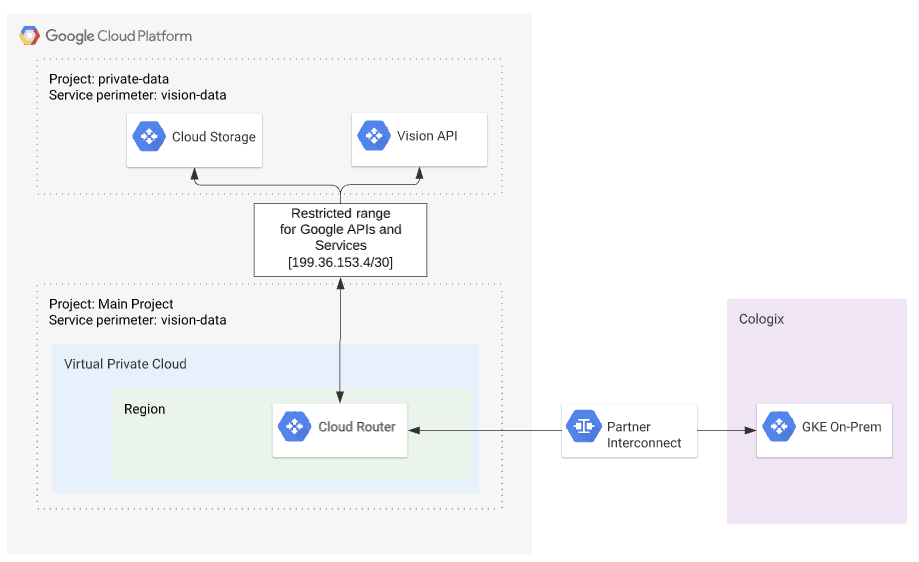
By creating a Service Perimeter containing the Cloud Storage API, Cloud Vision API, the Google Cloud Project(s) for Anthos GKE on VMware, Acme Co. can restrict access to only the services and service accounts required by the application. In addition, access to the GCS buckets where both the pre and post-processed documents reside is protected from unauthorized data access, and access to resources outside the perimeter is restricted. This prevents reading or copying of the data outside of the authorized environment.
By combining Private Google Access with a Cloud Interconnect, Acme Co. ensures that all traffic related to the application remains on well-known networks.
This combination of Service Perimeters, Private Google Access and Cloud Interconnect allows Acme Co to secure and audit the document environment throughout the application life cycle.
Are you considering Cloud Interconnect or creating service perimeters for your workloads? We’d love to help! Contact us to get started.
About the Author: Jenn Viau | Principal Cloud Consultant
Jenn brings almost two decades of experience in infrastructure, automation, configuration management, and architecture. In her previous roles, she worked with teams to design, deploy, and operate scalable, cloud-native platforms. Jenn is passionate about exploring new approaches, tools, and methodologies and helping customers find the “right” way and “right” tooling to get things done.
